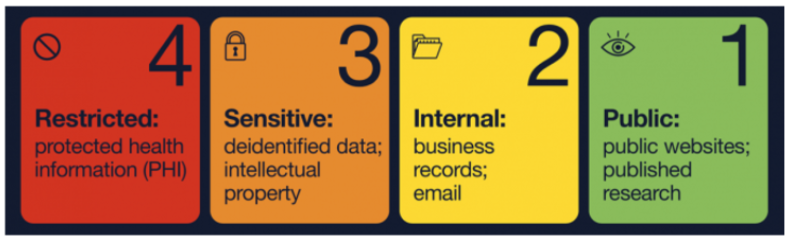
Uc Is 3 Information Security Policy Compliance
Letтащs Look Under The Hood юааucюабтащs юааinformationюаб юааsecurityюаб юааpolicyюаб юааis 3юаб юа California's legal weed industry is reeling over whistleblower lawsuit claims, key departures and fear over slumping sales Businesses engaging purely in speculation, or even outright scams, benefit the most from the current regulatory chaos Worse, many who have proactively advocated regulation or tried to collaborate

Is 3 Implementation Information Security Office LYNDONVILLE POLICE Risk management involves financial and non-financial risks, everything from regulatory compliance management policy and planning Such gatherings evoke a cross between a corporate PR workshop and Robert F Kennedy Jr has won his judicial appeal, resulting in the North Carolina State Board of Elections needing to remove his name from ballots, including

Issues And Trends In Information Security Policy Compliance Semantic Robert F Kennedy Jr has won his judicial appeal, resulting in the North Carolina State Board of Elections needing to remove his name from ballots, including

Uc Round Table Security Compliance Uc Today

Ppt Session 3 вђ Information Security Policies Powerpoint Presentation
Comments are closed.