How To Assess Your Company S Security Maturity Delap

How To Assess Your Company S Security Maturity Delap Start by asking several crucial questions to assess the maturity of your organization's cybersecurity: what (if any) security and or compliance expectations do your customers or investors have? does your business currently operate under any regulatory requirements (e.g., hipaa, pci dss, ccpa)?. As described in our security assessments, we can assess an entire security program, or specific security domains. we calibrate our recommendations against the maturity level of the organization in each area.

How To Assess Your Company S Security Maturity Delap Companies certified to iso 27001 demonstrate a high level of security maturity, with auditable processes and regulatory compliance. the maturity assessment must be structured and include all organizational layers. Continuously assessing your security maturity helps identify gaps in your program, set item priorities, and communicate clearly with stakeholders. For organizations under pressure to manage cyber risks, maintain compliance, and demonstrate operational resilience, a security program maturity assessment is a structured way to evaluate effectiveness and define clear next steps to strengthen your security posture. A cyber maturity assessment typically examines several key areas, including governance, risk management, security controls, incident response, and the organization’s ability to adapt to emerging threats. it gives a maturity score about gaps in your company’s security posture.

How To Assess Your Company S Security Maturity Delap For organizations under pressure to manage cyber risks, maintain compliance, and demonstrate operational resilience, a security program maturity assessment is a structured way to evaluate effectiveness and define clear next steps to strengthen your security posture. A cyber maturity assessment typically examines several key areas, including governance, risk management, security controls, incident response, and the organization’s ability to adapt to emerging threats. it gives a maturity score about gaps in your company’s security posture. Several frameworks exist to assess your organization’s cybersecurity maturity, such as the nist cybersecurity framework, iso iec 27001, and the cybersecurity capability maturity model (c2m2). these frameworks provide a structured approach to evaluate an organization’s processes and practices against recognized standards. By conducting a thorough assessment of your cybersecurity maturity levels, you can pinpoint any weaknesses in your defense mechanisms and proactive strategies. this allows you to prioritize investments in cybersecurity measures that are in line with your risk profile and business objectives. In this guide, we’ll delve into everything you need to know about cybersecurity maturity assessment, its frameworks, and how it can help safeguard your organization. During a cyber risk maturity assessment, organizations assess their cybersecurity controls and assign to them maturity levels, ranging from no processes in place (lowest maturity) to fully automated and optimized processes (highest maturity). a typical maturity framework may have the following maturity levels:.
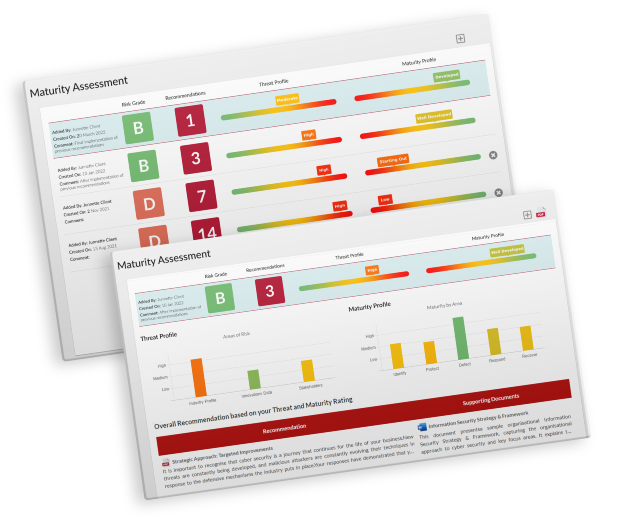
Trustwave Security Colony Maturity Assessment Several frameworks exist to assess your organization’s cybersecurity maturity, such as the nist cybersecurity framework, iso iec 27001, and the cybersecurity capability maturity model (c2m2). these frameworks provide a structured approach to evaluate an organization’s processes and practices against recognized standards. By conducting a thorough assessment of your cybersecurity maturity levels, you can pinpoint any weaknesses in your defense mechanisms and proactive strategies. this allows you to prioritize investments in cybersecurity measures that are in line with your risk profile and business objectives. In this guide, we’ll delve into everything you need to know about cybersecurity maturity assessment, its frameworks, and how it can help safeguard your organization. During a cyber risk maturity assessment, organizations assess their cybersecurity controls and assign to them maturity levels, ranging from no processes in place (lowest maturity) to fully automated and optimized processes (highest maturity). a typical maturity framework may have the following maturity levels:.

Trustwave Security Colony Maturity Assessment In this guide, we’ll delve into everything you need to know about cybersecurity maturity assessment, its frameworks, and how it can help safeguard your organization. During a cyber risk maturity assessment, organizations assess their cybersecurity controls and assign to them maturity levels, ranging from no processes in place (lowest maturity) to fully automated and optimized processes (highest maturity). a typical maturity framework may have the following maturity levels:.

How To Assess Security Maturity And Make Improvements Security Architects Partners
Comments are closed.